Bitcoin takes advantage of the Unspent Transaction Output (UTXO) product, corresponding to transactions with Actual physical hard cash where by each individual Monthly bill would wish being traced. On other hand, Ethereum works by using an account design, akin into a bank account having a running equilibrium, which happens to be additional centralized than Bitcoin.
Unlock a globe of copyright trading chances with copyright. Working experience seamless trading, unmatched reliability, and steady innovation on the platform created for both equally inexperienced persons and professionals.
As soon as that?�s accomplished, you?�re Completely ready to convert. The exact techniques to accomplish this process fluctuate based upon which copyright platform you use.
Enter Code even though signup to receive $a hundred. I have been applying copyright for two years now. I actually appreciate the changes from the UI it received over the time. Believe in me, new UI is way better than Other people. Nevertheless, not every little thing On this universe is perfect.
??Also, Zhou shared which the hackers begun using BTC and ETH mixers. As the identify indicates, mixers combine transactions which even more inhibits blockchain analysts??capability to monitor the funds. Subsequent the use of mixers, these North Korean operatives are leveraging peer to see (P2P) sellers, platforms facilitating the direct order and offering of copyright from 1 person to a different.
copyright.US is just not chargeable for any loss that you just may well incur from price tag fluctuations any time you acquire, market, or maintain cryptocurrencies. Please refer to our Conditions of Use To find out more.
Hi there! We noticed your evaluate, and we desired to Test how we may aid you. Would you give us extra particulars regarding your inquiry?
Trade Bitcoin, Ethereum, and in excess of one hundred fifty cryptocurrencies and altcoins on the ideal copyright System for small service fees.
Information sharing businesses like copyright ISAC and SEAL-ISAC, with partners over the copyright industry, get the job done to improve the pace and integration of efforts to stem copyright thefts. The marketplace-broad reaction towards the copyright heist is a fantastic illustration of the value of collaboration. Nevertheless, the necessity for ever speedier action stays.
This incident is much larger than the copyright business, and this kind of theft can be a make a difference of world protection.,??cybersecurity steps may perhaps become an afterthought, especially when businesses lack the money or personnel for this kind of measures. The issue isn?�t special to Individuals new to organization; even so, even properly-proven firms may possibly Allow cybersecurity drop towards the wayside or might lack the instruction to be familiar with the fast evolving menace landscape.
TraderTraitor and various North Korean cyber risk actors continue on to more and more deal with copyright and blockchain organizations, mainly because of the lower risk and substantial payouts, versus targeting money establishments like banking institutions with demanding stability regimes and polices.
On top of that, reaction instances could be improved by making sure persons Doing work throughout the agencies linked to avoiding monetary criminal offense get instruction on copyright and the way to leverage its ?�investigative electric power.??
Seeking to go copyright from a different platform to copyright.US? The subsequent measures will guideline you through the method.
Policymakers in The usa really should in the same way utilize sandboxes to try to locate simpler AML and KYC remedies for that copyright Place to be certain effective read more and efficient regulation.
Enter Code when signup to obtain $one hundred. Hey guys Mj in this article. I often start with the place, so below we go: occasionally the application mechanic is complexed. The trade will go on its facet the other way up (when you stumble upon an connect with) however it's rare.
These danger actors have been then in a position to steal AWS session tokens, the non permanent keys that allow you to request non permanent qualifications for your employer?�s AWS account. By hijacking Energetic tokens, the attackers ended up capable of bypass MFA controls and achieve use of Harmless Wallet ?�s AWS account. By timing their endeavours to coincide Using the developer?�s regular perform hrs, Additionally they remained undetected right up until the particular heist.
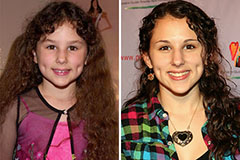 Hallie Eisenberg Then & Now!
Hallie Eisenberg Then & Now! Hailie Jade Scott Mathers Then & Now!
Hailie Jade Scott Mathers Then & Now! Raquel Welch Then & Now!
Raquel Welch Then & Now! Kane Then & Now!
Kane Then & Now! Daryl Hannah Then & Now!
Daryl Hannah Then & Now!